News
Photo courtesy of Flickr user Garrett Coakley.
 Rachel Greenstadt ’07 (Ph.D.) is an Assistant Professor of Computer Science at Drexel University, where she runs the Privacy, Security, and Automation Laboratory. Her research group aims to develop autonomous systems that are trustworthy enough to handle sensitive data and important decisions.
Rachel Greenstadt ’07 (Ph.D.) is an Assistant Professor of Computer Science at Drexel University, where she runs the Privacy, Security, and Automation Laboratory. Her research group aims to develop autonomous systems that are trustworthy enough to handle sensitive data and important decisions.
Her interdisciplinary research currently involves the way machine learning technologies interact with security and privacy problems. In particular, she investigates whether algorithms can identify individuals by their linguistic writing style and whether individuals can, in turn, modify their style to evade such detection.
What problem interests you the most in the area of personal data privacy?
I am deeply interested in how the ease of storing, transferring, and analyzing electronic data changes the balance of power in our society, particularly the power between large organizations and individuals, but also our intimate social relationships. How we respond to these changes, both in terms of institutions and technologies, will affect what sort of society we become.
Why is it important to work in the field of privacy and information security?
There exists a huge tension between increased productivity on the one hand and security and freedom on the other. Increases in computing power, interconnectedness, and data storage and analytics have led to ongoing gains in productivity, which is great, but they have created a problem where these features outrun security and privacy concerns.
There are security problems in the whole computing infrastructure, but we keep doing more with it and hooking up more physical things to it because the gains we realize are so large. But they come at a price.
Similarly, to exist as a social person in our society increasingly requires the release of large amounts of information both to large organizations and to neighbors. So it is important to work in this field to push back against these trends, and explore how we can realize these gains without compromising privacy or security.
How did completing your graduate work at Harvard prepare you for success in your career?
At Harvard, I was able to develop as an independent researcher. My adviser encouraged me to define my own projects and work with multiple student and faculty collaborators. This has really helped me be successful as a young professor.
Harvard’s strong reputation in multiple fields is helpful to anyone who wants to work in interdisciplinary areas. My degree is very broadly respected. Harvard CS is a small department, and I was able to learn from and collaborate with multiple faculty members in different fields. I had a great relationship with my adviser, Mike Smith, but I was also mentored by Barbara Grosz, David Parkes, Mema Rosoupoulos, H. T. Kung, Greg Morrisett, and Stuart Shieber.
People were really willing to mentor me. But, more than that, I was able to work with faculty and students at the Kennedy School, at the Law School, and in the math and government departments while I was there, and that experience broadened my perspectives and skill sets.
What accomplishment are you most proud of since receiving your Ph.D.?
I was selected to join the DARPA Computer Science Study Group, which is a group of 12 junior faculty members and consists of a funded educational experience to familiarize the participants with Department of Defense practices, challenges, and risks, and up to three years of funded research to explore and develop technologies that have the potential to transition innovative and revolutionary computer science and technology advances to the government.
This program has provided a tremendous opportunity to build up and develop my research lab, but also given me an opportunity to expand my horizons (including jumping off a 34-foot paratrooper training tower) and serve my country.
There are relatively few women working in computer science, though that is changing with the current generation of students. Has gender ever been an issue for you, in your career?
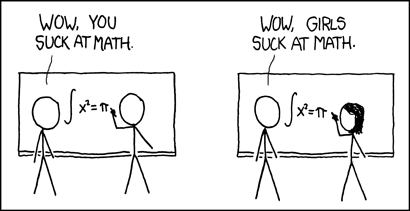
I'm always reminded of the xkcd comic called “How it Works” by Randall Munroe (below). I think the low representation leads to a kind of pressure to represent your gender, and I feel that in my successes, failures, and choices.
I have strongly benefited from both male and female mentors and role models throughout my career, but I know that some women can feel very isolated. I have made an effort through the Women in Computing Society at Drexel (WiCS) and involvement in the Grace Hopper Conference to pay it forward and help alleviate that for younger women.
How did you first get interested in information privacy and security?
My friends and I used to participate in a competition called History Day, and in eighth grade we did a project looking at cryptography as used in the Pacific War in World War II (lots of people pay attention to the Enigma machine and Bletchley Park, but pay less attention to the importance of codes to the Pacific War, particularly in the Battle of Midway). I found it really interesting, and I borrowed a library book that had some BASIC programs for encrypting and decrypting data, typed them into my Apple IIe, and used it to play with making secret messages.
This is the sort of story that makes it look like I knew what I wanted to do at a very early point, but that is not the case at all. At the time, I thought I wanted to be either an architect or a science fiction writer, and I had similar bouts of intense interest in ancient Egypt, the Dadaist art movement, and the arts and crafts movement in early 20th-century architecture. I think it’s important to point this out because many young people (particularly young women) seem to have this belief that you have to have a narrow focus to do computer science, and that is not true.
What advice would you give a Harvard computer science student today?
Take advantage of the whole department and the whole university. There is so much opportunity for learning and growing here. Take the initiative with your research direction, and make sure to enjoy yourself.
What memory stands out the most from your time at Harvard?
I was a member of the Harvard-Radcliffe Science Fiction Association, and through that I met some undergrads. In my first year of graduate school, we were hanging out in Lowell House and talking about why people don’t read privacy policies on web sites. So we were two computer scientists and a government major, and we decided to try to model the problem game theoretically. It was really fun to find that result, working with friends in the interstitial spaces between fields.
The paper that came out of that is one of my most cited papers.
Topics: Computer Science
Cutting-edge science delivered direct to your inbox.
Join the Harvard SEAS mailing list.



